What if you could take massive action on your data as your organization grows and new challenges emerge?
Apply Policy-Based Automation for:
-
Lifecycle Data Management driven by Identity Management
- Home Folders
- Group File Shares
-
Data Footprint Reduction
-
Archiving and Grooming
-
Migrations and Restructuring
-
Orphaned Data Reconciliation
What effect would a faster and more complete response to these types of challenges have?

If you are running a Microsoft Windows Server ecosystem of any size or complexity, you need to apply policy and scalable automation to your data. If you don’t, it won’t be long before chaos ensues and you have a hard time staying on top of things, especially with compliance goals.
We’ve been developing, refining, and adapting our turn-key technology to ever-evolving real-world use cases in the largest organizations around the world for 20 years.
As you read this, our technology is managing data for millions of people.

Our Goals for You
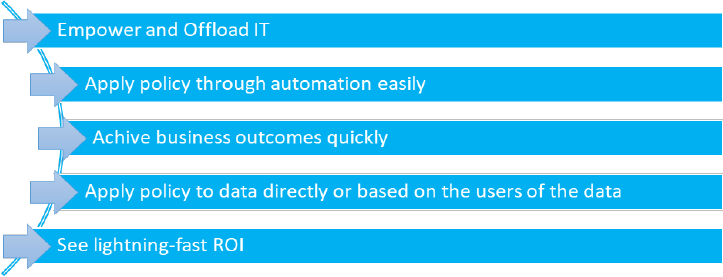
Apply Policy on Your Terms…

A) Identity-Driven
Apply policy to data based on the people that use it.
Completely automate Home Folder management (including cleanup) for users
Automatically build and dynamically manage Collaborative Storage for groups

B) Target Data-Driven
Apply policy to specific target data based on needs.
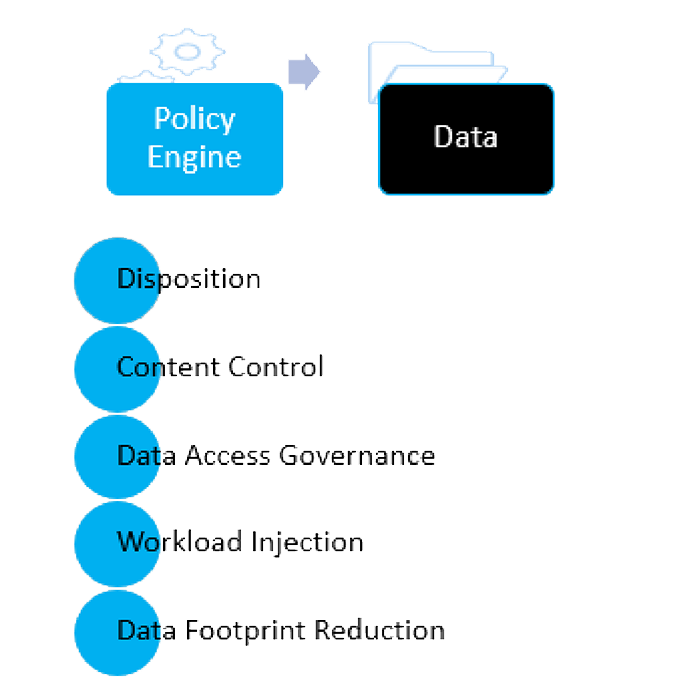
Achieve goals around management, governance, and compliance.
Click on the tabs at the top to learn more details about how we help, specific challenges that might align with your goals, and some case studies of how Data Management has helped a few of our other customers.
Organizations Need Automated Data Management
The expanding responsibilities associated with data management are requiring that organizations look to automation. Automation not only saves time and money, it can keep organizations protected from data breaches and even ransomware attacks, help organizations with compliance to data storage regulations, assure that users have the right access permissions, provision network storage for users and groups, clean up expired data, and much more. So, how is Condrey Corporation today automating data management at hundreds of customer sites with millions of users?
Policy-Based Management
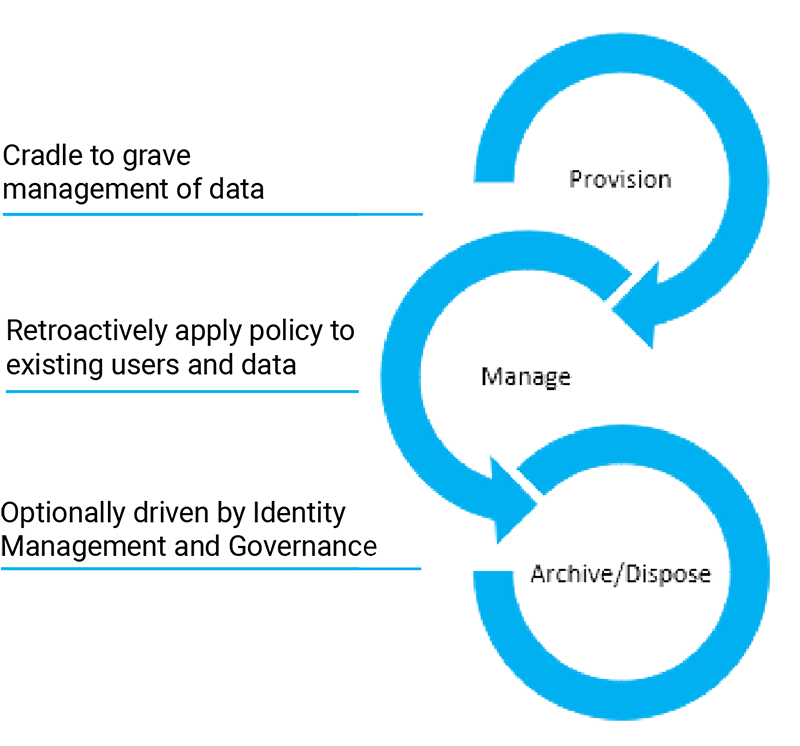
Most organizations have written policies or rules on how to manage its data – especially its sensitive and high-value data. Condrey Corporation technology lets you take these rules from paper and enforce them through its Senergy product. Senergy policies can be created for how to clean up expired data, enabling user access to Windows network folders storing sensitive and high-value data based on a user’s role, the size, location, and contents of a Windows network home folder provisioned for a new user, and many other types of policies.
Windows File System Automation
Once these policies are established in Senergy, their specifications are strictly enforced. In many cases, these actions take place automatically when an event in Active Directory takes place. For example, when a user leaves the organization and the user object is removed from Active Directory, rather than have the user’s home folder remain on primary storage as an “orphan folder,” the policy can automatically archive the folder by moving its contents to a vault location where the former user’s manager can review its contents before deletion.
In other cases, a network administrator can invoke the actions of a policy to enforce the policy’s specifications. For example, performing a policy enforcement can move a user’s personal music and media files from primary storage to an archive location.
Policy-Based Management for All Types of Data
Senergy enables organizations to create both Identity-Driven and Target-Driven policies. Identity-Driven policies automate storage management tasks that are enacted through an association with Active Directory users, groups, and containers. These include user home folders and group collaborative project folders. Target-Driven policies manage and perform tasks through direct association with a network share or folder. An application-specific folder, a folder storing sensitive legal documents, or a folder storing financial information that needs to be restricted to only authorized users can all be managed and secured through Target-Driven policies.
Supports Existing IAM Systems
Many organizations use identity and access management (IAM) systems to control user access to critical structured data within their organizations. For example, through Active Directory identity attributes, the IAM system enables or restricts user access to applications and associated records – many of which contain private information that need to be secured.
The technology in Condrey Corporation’s Senergy product was engineered to complete the identity management chain by simultaneously provisioning user storage and access to unstructured data, as the IAM system provisions access to structured data. Senergy does not require an IAM system to provision and manage storage, but it offers an even more compelling data management story when working with an IAM system.
Return on Investment
Most organizations that have deployed Senergy quickly realize the amazing ROI from the product. Whether it’s by automating thousands of hours of manual work and doing so in a consistent and auditable manner, alleviating personnel from doing mundane, error-prone storage jobs, assuring that users have access to the storage resources they need, automating NTFS management and Windows cleanup, or providing organizations the confidence that their storage is secure and available, the data management technology found in Senergy tends to remain a long-term fixture at organizations where it is deployed.
Research indicates that despite all of the benefits of cloud storage, most organizations are not migrating all of their data to the cloud. Rather, they are adopting a hybrid arrangement between cloud and on-prem storage. While the reasons for dispersing the storage of some files to the cloud and others…
Read MoreProtecting an organization’s data assets is more than securing sensitive and confidential information residing in application databases to meet compliance regulations. It should extend to the unstructured data – the word processing, spreadsheets, presentations, and media files that contain proprietary and intellectual information whose unauthorized access or loss could be…
Read MoreNo one knows the value, relevance, or sensitivity of the information in a file as much as someone who works with that file. A manager in an HR Department for example, knows much more about a spreadsheet of employees than an IT Department worker. By utilizing the knowledge and input…
Read MorePerforming Large-Scale Data Operations Organizations are storing more data than ever. With over 80 percent of an organization’s data being unstructured data, larger organizations can be storing petabytes of word processing files, spreadsheets, presentations, media, and other files that need to be secured, moved, deleted, or archived. The challenge is…
Read MoreMigrating data has always been a part of IT. And while one of the biggest business drivers today is mandates to move on-premises stored data to the cloud, less extreme storage migrations take place on a regular basis such as when new servers or NAS devices are deployed, servers are…
Read MoreIt’s a threat that has the power to literally shut down your organization’s operations. Through nefarious means, cyber criminals access your network and install malicious encryption software designed to block you from accessing your data by holding it “hostage” until you pay a ransom. Organizations of all sizes and in…
Read MoreData Management Requirements Different data sets require different management approaches. An application folder on the network storing application-specific files needs to be managed in a way that older files do not conflict with new ones when application software is updated. In this example, older application files might need to be…
Read MoreA U.S. based insurance company’s challenges of keeping sensitive account information located in unstructured data away from unauthorized users has been solved, thanks to a combined deployment of Galileo and Senergy for a Data Access Governance solution. Before deploying the two products, the insurance company did not have the confidence…
Read MoreA state land office in the United States needed both file system data and file system permissions included in the same report. This report was needed to demonstrate compliance to state requirements for access restricted to only authorized users. Because they are easily generated as built-in reports in Galileo, File…
Read MoreA software developer was in the process of consolidating servers and needed to identify those files that were relevant and needed to be migrated to one of the new servers, and those files that were less relevant and could be archived or deleted. They decided to base the migration decision…
Read MoreMigrating student home folders from one set of servers to another is normally an arduous event. But for one U.S. university’s IT department, it turned out to be easier than they could imagine. The university had been using Senergy from Condrey Corporation for years to automatically provision student home…
Read MoreThe Challenge Like most regulated industries, banks are required to protect the privacy of consumers’ finances under a federal law called the Financial Modernization Act of 1999 (also known as the Gramm-Leach-Bliley Act). The law governs how financial institutions can collect and disclose customers’ personal financial information, maintain safeguards to…
Read More
Senergy
Automate the Management & Protection of Your Network File System Data
Automate data management to mitigate risk. Identity-Driven and Target-Driven policies in Senergy ensure that you’re always managing data assets properly. Senergy handles data privacy, rights and access analysis, data disposition, and protection of high-value targets through its policies.
Galileo
Discover and Analyze What You're Storing and Who Has Access to It
Unstructured (file-based) data makes up more than 80 percent of an organization's stored data. Galileo inventories and analyzes files stored on your network and in Microsoft 365 repositories, so you have the information you need to optimize and secure your stored files.