What if you could be confident that the people in your organization have access to the data they need? …and don’t have access to data they shouldn’t?
What if Line-of-Business Data Owners could have the same confidence and the tools to be informed and engaged?
What would that mean for your organization and your people?

Lots of organizations have been busy working on application management to protect data.
Did you know that unstructured data like the files in your Microsoft Windows Server ecosystem account for about 80% of a normal organization’s data footprint?

The most vital data to many organizations include things like:
These are the crown jewels of an organization…and they normally live in files as unstructured data.
What are your crown jewels? Where do they live?
When it comes to security, let us help bring order to disorder!
The great news is that you don’t have to boil the ocean to improve your security posture!
Step 1) Discovery: Insight and Understanding
With our Data Insight solution, you will be able to work, optionally with the Line-of-Business Data Owner, to understand the current state of security for each data location holding your crown jewels. From that insight, you will be able to make informed strategic decisions and meet audit request goals.

Step 2) Straighten Up: Correct Discovered Issues
It is highly likely that you will find things in the discovery phase that are important to correct. You will be able to do that with a high degree of confidence.

Step 3) Continuous Governance: Implement Policy through Automation
Straightening up is good, but keeping things straight is the best. You will be able to develop policy for protecting each of your crown jewels and implement that policy so that it is automatically applied on your terms, even if that policy only dictates that you and/or data owners stay informed about security changes as time passes.
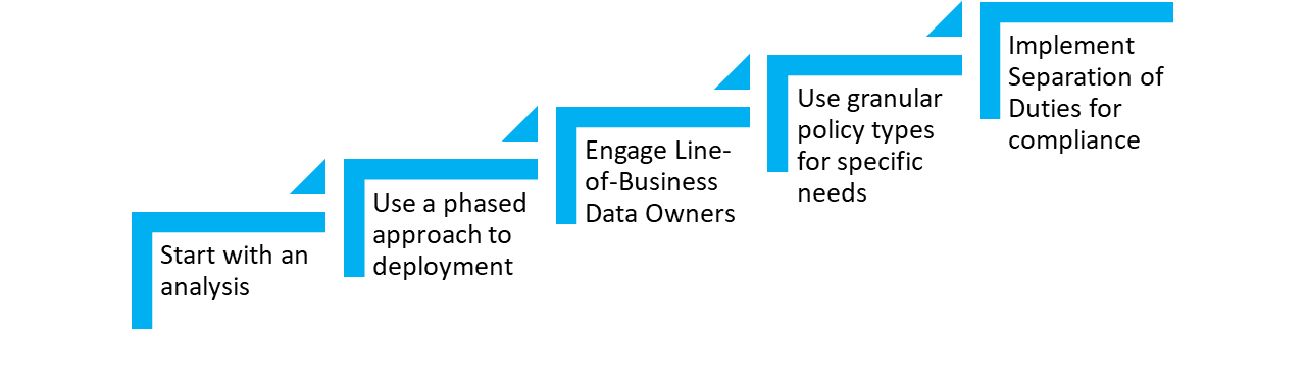
You can use a phased approach in two ways
Business outcomes that matter
Let’s improve your overall security posture with your data.
So you have less chance of it falling into the wrong hands…
…and so that people that need access to do their job have it. .
Don’t be overwhelmed…
Click on the tabs at the top to learn more details about how we help, specific challenges that might align with your goals, and some case studies of how Data Access Governance has helped a few of our other customers.
The need for an Integrated, Automated Approach
The scope of Identity Governance and Administration (IGA) is expanding. In the past, the primary focus of permissions and entitlement management was on applications and associated data. Later, Identity Governance (IG) applications were the means of conducting access reviews for assuring that only authorized users had access to these applications and data.
But sensitive data is also contained in file-based data stored on networks and the Microsoft 365 cloud. Unauthorized access to this data can result in everything from data breaches to ransomware.
Data Access Governance (DAG) is a market segment that focuses on identifying and addressing the malicious and non-malicious threats that can come from unauthorized access to sensitive and valuable unstructured data. Condrey Corporation, through its integrated Senergy and Galileo products, uses an identity-based approach to:
- Determine if sensitive and valuable files are being stored in secure locations
- Identify who has access to these files
- Correct and enforce access permissions
Network- and Cloud-Stored Data is Vulnerable
Sensitive and high-value data is not just the Personal Identifiable Information (PII) stored as records in your applications’ databases. It’s sales data on spreadsheets, legal documents in word processing files, upcoming marketing campaigns in presentation files, and more. Keeping these files from being accessed by unauthorized users is therefore critical to the success of the organization.
Risks of Improper Access Permissions
Highly functional and secure organizations recognize that access to network locations needs to be based on user identity and role. Doing so enables the right users to access the files they need to do their work while restricting the wrong users from accessing sensitive and high-value data that they should not have access to. Furthermore, restricting user access to only those network areas they should have access can significantly reduce the risks of a ransomware virus propagating throughout the organization’s network file system.
Data Access Governance Market Segment
After many high-profile instances of data breaches at prominent organizations, security analysts are recognizing the vulnerability of sensitive and high-value data stored on network file systems. In fact, information research organizations such as Gartner have identified Data Access Governance as a market segment focused on the identification and security of an organization’s unstructured data.
Engineered to Identify and Remediate Access Issues
The Data Access Governance solution from Condrey Corporation includes technologies for identifying the data you’re storing and providing you the details to make decisions on what to do with it. It then provides the means for taking automated remediating action. These actions include moving files to more secure locations, changing the access of permissions of network folders or shares, archiving or deleting expired files, removing duplicate versions of files, and much more.
Addresses Compliance Objectives
Mention the word “compliance” and most people think of regulations for keeping personal records safe from unauthorized users. HIPAA, for example, is one such regulation for protecting PII in the medical and insurance industries. But organizations also have their own rules for governing their data – rules such as who can access what files, how long to retain files, where they should be stored, etc. The problem is, these policies tend to be written but too difficult to enforce. The Condrey Corporation Data Access Governance solution is engineered to implement these “too difficult to enforce” rules through automated policies.
Works with Identity Management Systems
Similar to how Identity Management (IAM) systems grant and restrict user access to applications based on identity and role, Condrey Corporation’s Data Access Governance (DAG) solution grants and restricts user access to network storage areas based on identity and role – and it can do so as the IAM system provisions access to the application. For example, when an organization hires a new employee to work in the Accounting Department and grants access to accounting applications, the Condrey DAG solution can simultaneously provision user storage and grant access to storage areas on the network designated for the organization’s accountants.
Assists with Other Security Measures
For organizations with plans to implement security measures such as zero trust or the principle of least privilege (PoLP), DAG can assist in this effort by providing detailed NTFS security and permissions findings to help determine what courses of action should be taken to implement zero trust and PoLP.
Data Management Requirements Different data sets require different management approaches. An application folder on the network storing application-specific files needs to be managed in a way that older files do not conflict with new ones when application software is updated. In this example, older application files might need to be…
Read MoreThink bigger! Yes, cleaning up ROT is important. Redundant, Outdated, and Trivial files represent a chance to reduce your data footprint. Bigger problems exist out there in terms of data management and data compliance. When it comes to data cleanup, you have to worry about MORE (Misplaced, Orphaned, Risky, and…
Read MoreSensitive files are not just those files containing personal identifiable information (PII), they’re also the files that contain sales forecasts, financial numbers, and other strategic content to provide a competitive advantage for the organization. This information is frequently stored in spreadsheets, presentation files, and word processing files that are collectively…
Read MoreIt’s a threat that has the power to literally shut down your organization’s operations. Through nefarious means, cyber criminals access your network and install malicious encryption software designed to block you from accessing your data by holding it “hostage” until you pay a ransom. Organizations of all sizes and in…
Read MoreNo one knows the value, relevance, or sensitivity of the information in a file as much as someone who works with that file. A manager in an HR Department for example, knows much more about a spreadsheet of employees than an IT Department worker. By utilizing the knowledge and input…
Read MoreA U.S. based insurance company’s challenges of keeping sensitive account information located in unstructured data away from unauthorized users has been solved, thanks to a combined deployment of Galileo and Senergy for a Data Access Governance solution. Before deploying the two products, the insurance company did not have the confidence…
Read MoreA large U.S. headquartered advertising conglomerate with multiple agencies has more than one hundred thousand employees and hundreds of partners in the management of its clients throughout the world. To manage the complexity of its global IT requirements, the conglomerate depends on an outsourced IT department for overseeing its hundreds…
Read MoreA school district in the United States found that its servers were infected with a cryptovirus. The virus encrypted and inserted the word “decrypt” into the filenames of all affected files. The party responsible for the cryptovirus demanded that the school district pay a ransom in order to get the…
Read MoreThe Challenge Like most regulated industries, banks are required to protect the privacy of consumers’ finances under a federal law called the Financial Modernization Act of 1999 (also known as the Gramm-Leach-Bliley Act). The law governs how financial institutions can collect and disclose customers’ personal financial information, maintain safeguards to…
Read More
Senergy
Automate the Management & Protection of Your Network File System Data
Automate data management to mitigate risk. Identity-Driven and Target-Driven policies in Senergy ensure that you’re always managing data assets properly. Senergy handles data privacy, rights and access analysis, data disposition, and protection of high-value targets through its policies.
Galileo
Discover and Analyze What You're Storing and Who Has Access to It
Unstructured (file-based) data makes up more than 80 percent of an organization's stored data. Galileo inventories and analyzes files stored on your network and in Microsoft 365 repositories, so you have the information you need to optimize and secure your stored files.

